CIS Faculty Technology Blog
Matthew Migration
All files previously stored on Matthew should now be migrated to SharePoint or be in read-only mode for a short while until the old storage platform is retired. If you still rely on access to any files on Matthew, please contact cis-bst@spu.edu so you don’t lose access to those files.
Zoom Client Upgrade
Zoom will be deprecating older versions of the Zoom client over the next few months. To prevent disruption, we have updated academic computers and podiums with the latest version and have made the new version available in Software Center.
We recommend you ensure your computer is setup to receive automatic updates and is on the latest version of the desktop client. To check the version you have installed or to download the latest version, please take some time now to make sure your computer is ready by following the steps below:
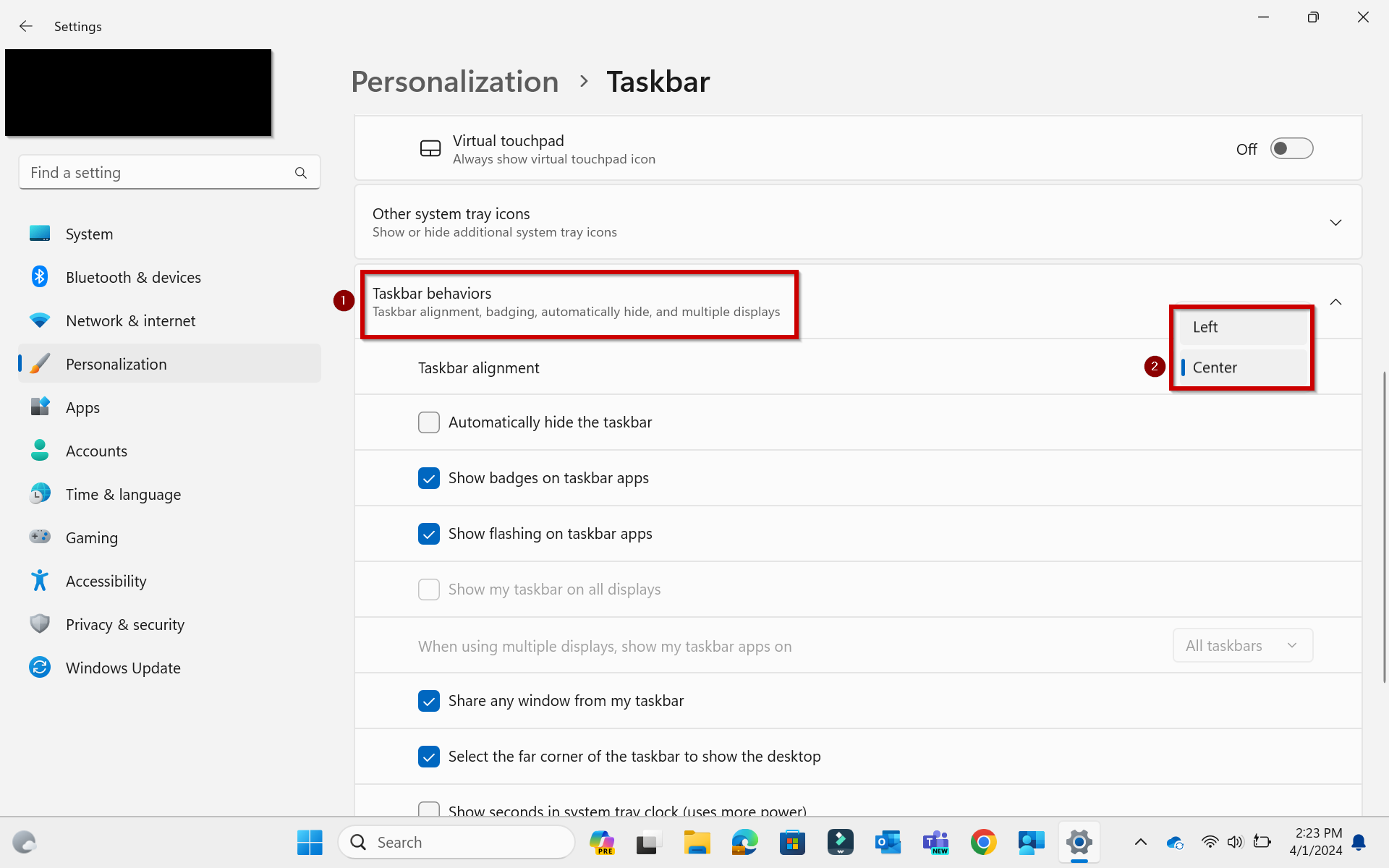
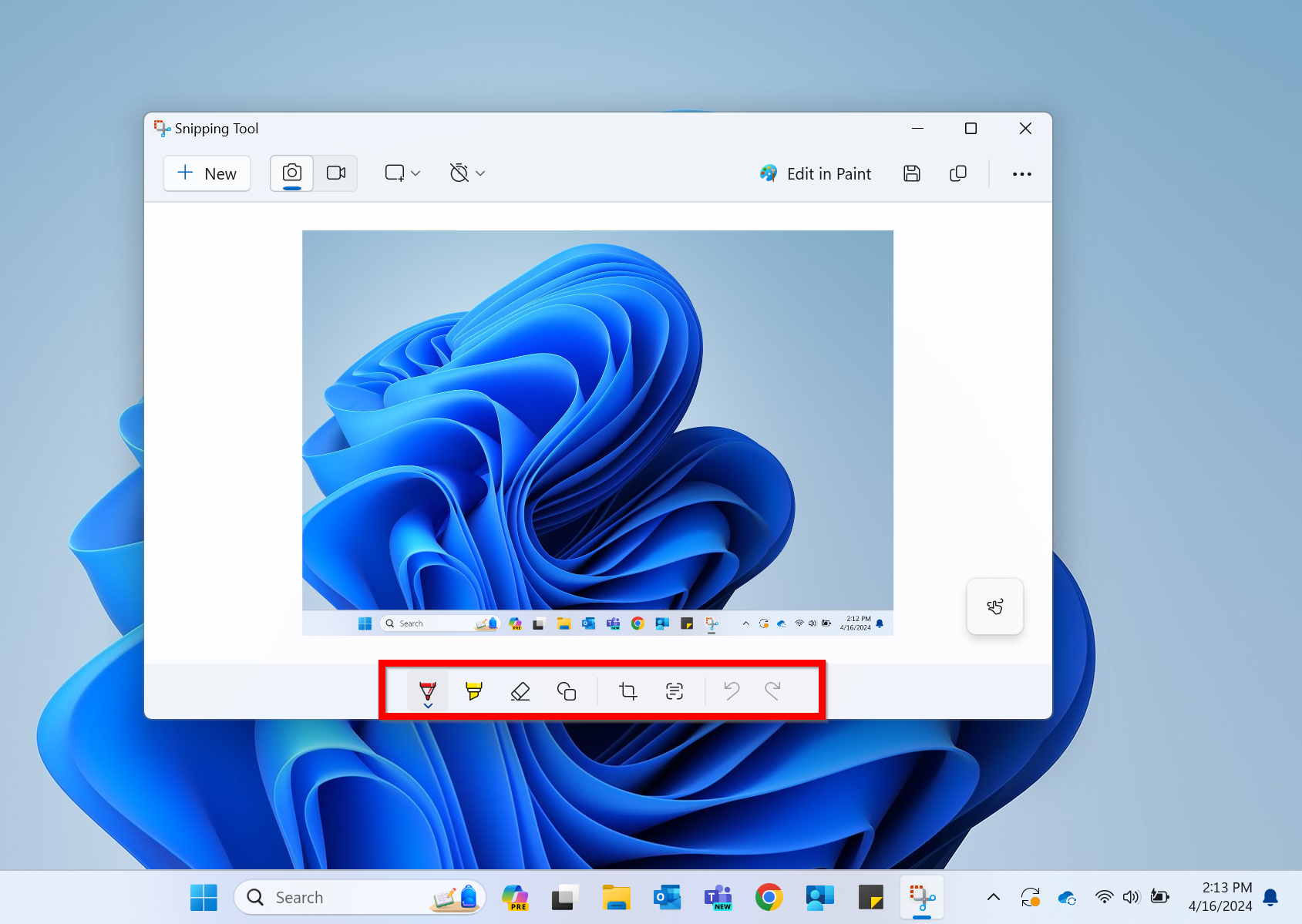
Once signed in, select your profile photo in the top right corner.
Select Check for updates. If there are updates available, Zoom will download and install.
If you have additional questions or concerns, please reach out to the CIS HelpDesk at help@spu.edu or at 206-281-2982.
Classrooms and Labs
Demaray 356 Updates
Demaray 356 is transitioning into an integrated hybrid pilot classroom! This pilot room space will be used to test a new integrated hybrid system. Previously installed hybrid classrooms did not have an integrated PC with the system, whereas the new system being trialed has an integrated system that you can plug your laptop into.
If you’re interested in learning more about how the room works or would like to have a demo of the classroom, please reach out to CIS at help@spu.edu!
Academic PC Software
CIS is in the process of rolling out Windows 11 for all of campus! We are also collecting software requests for fiscal year 2024-2025.
For questions or concerns regarding the Windows 11 rollout and how it may impact academic lab spaces and/or classroom podium pcs, individuals can collate their requests for their department via submitting software requests form here: Software Requests ‘24-25.
If you are concerned about specific software compatibility with Windows 11, such as specialty hardware or legacy software, please complete the form linked above.
As a reminder, we encourage you to reach out the CIS HelpDesk if you have any questions or concerns at help@spu.edu.
Deployment for Windows 11 devices has begun! It has been announced that Microsoft will cease support for Windows 10 by the end of 2025, so CIS is proactively initialing our Windows 11 deployment process to stay ahead of the curve.
While Windows 11 has been available for a couple of years now, we understand that it may be new to some of you who have not yet upgraded. Our goal is to ensure a smooth and comfortable transition for all users. With this, you can find many helpful resources below!
Windows 11 Wiki Documentation
Documentation for Windows 11 is now available on the SPU Wiki as we begin processing deployments. This may serve as a valuable resource for anyone needing guidance on navigating the new system. Additionally, we have provided walkthrough videos to assist you in familiarizing yourself with Windows 11.
Microsoft Copilot
We are also going to introduce Microsoft Copilot, and encourage faculty and staff to consider leveraging this powerful AI tool within their work processes. Copilot can significantly enhance workflow efficiency, and understanding its functionality is increasingly valuable in today's AI-driven landscape. Documentation for Copilot is also accessible on the SPU Wiki for those interested in learning more.
Upgrade Checklist
To ensure a seamless transition during the deployment of updated Windows 11 devices, we've prepared a checklist for you to review before your visit to the HelpDesk. Once you've completed the checklist, there will be a link to schedule an appointment to receive your upgraded Windows 11 device. Please note that your previous laptop will be retained for one week to ensure that all data has been transferred successfully.
Faculty and Staff will be notified by the HelpDesk when to begin preparing for their device upgrades via email.
Windows 11 and Copilot Tips and Tricks
As deployment commences, we will be posting a weekly series of tips and tricks to help guide you through the transition and discover new efficient ways to enhance your work productivity. You can find the series of tips and tricks for Windows 11 and MS Copilot below:
How to add Another Account
The new Microsoft Teams allows for multi-account support, meaning you will be able to add another account to your Microsoft Teams App.
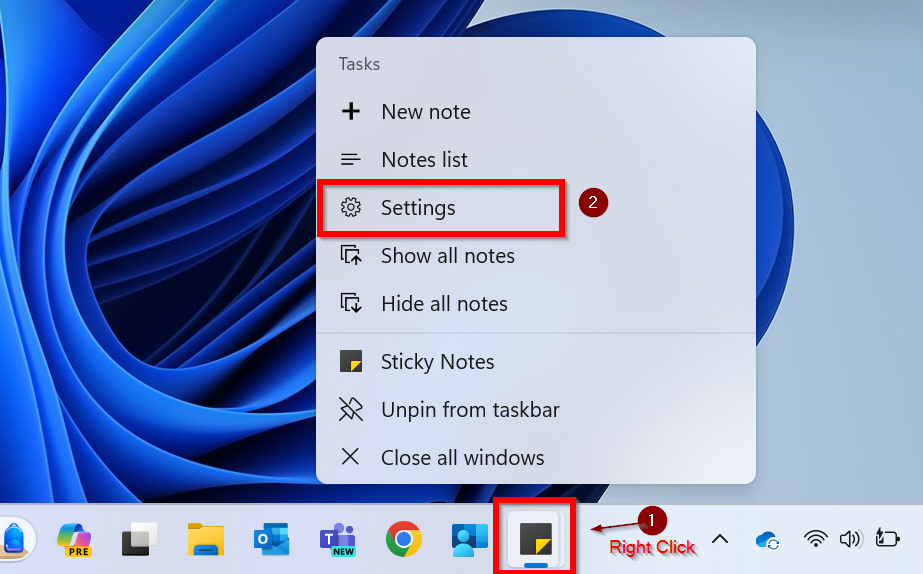
To add a new account, select your profile picture at the top right of the application window. Then, select Add another account.
Adding another account to your Microsoft Teams desktop app will allow you to get notifications for both accounts, in real time.
You will be able to participate in different chats, calls, and meeting without having to manually switch between accounts.
You will also be able to set your status for each account individually.
For a more in-depth explanation of how to add another account, please visit Manage Accounts and Organizations in Microsoft Teams, or by following the link below:
Other Microsoft Teams-related Updates
View what else is new by following the link: Microsoft What's New in Teams.
Also, linked below is the starting video in Microsoft Teams Youtube Playlist covering Microsoft Teams:
How Microsoft Teams Used to Look:
October is Cybersecurity Awareness Month - CSA
It is CIS's responsibility to share some vital information about how to be safe while using the internet and managing yours and students' information.
Over the next few weeks, CIS will be releasing a weekly blog post that expands on four core topics for this year's CSA month: Phishing, Social Engineering (whaling), Passphrases for passwords, and Ransomware.
At the end of the month, there will be a quiz released to employees and students. Receiving 100% on the quiz will automatically enter the user into a raffle. The raffle will have two winners, one student and one employee, who will each receive a prize* from CIS!
Keep an eye out for the first blog post on October 9, and then every following Monday until the end of the month!
*Please note that prizes will be ordered once they are selected by the prize-winners. CIS will contact prize-winners when the prizes are ready to be picked up from the HelpDesk.
Security Awareness Week 1: Phishing emails
What is Phishing?
Often carried out over email -- although the scam has now spread beyond suspicious emails to phone calls (so-called "vishing"), social media, SMS messaging services (aka "smishing"), and apps -- a basic Phishing attack attempts to trick the target into doing what the scammer wants.
Exactly what the scammer wants can vary wildly between attacks. It might be handing over passwords to make it easier to hack a company or person, or sending payments to fraudsters instead of the correct account. This information is often stolen by making requests that look entirely legitimate -- like an email from your boss, so you don't think twice about doing what is asked.
How would you identify a Phishing email?
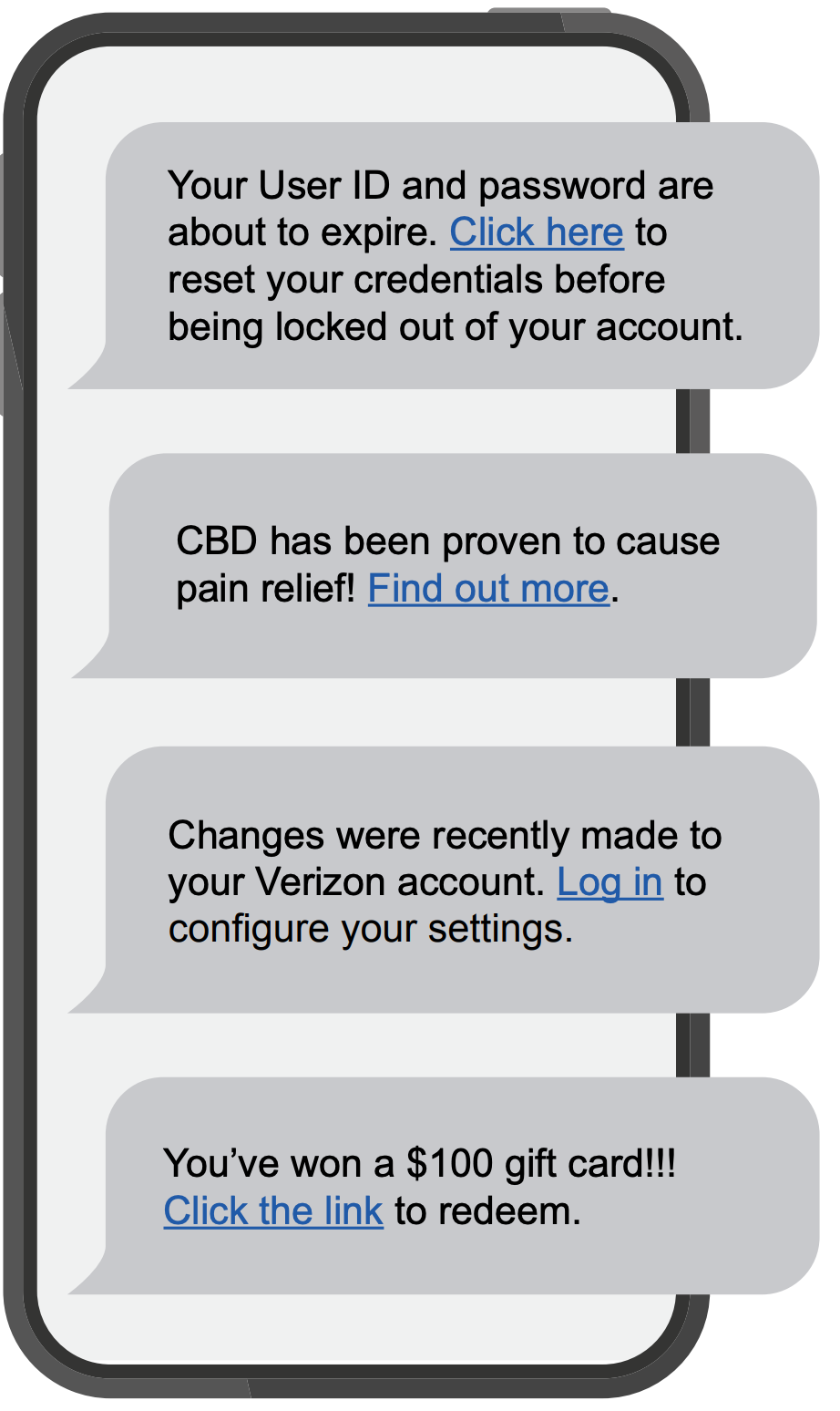
Emails that contain the following should be approached with extreme caution, as these are common traits of phishing email:
- Urgent action demands.
- Multiple sources in the from email address line.
- Poor grammar and spelling errors.
- An unfamiliar greeting or salutation.
- Requests for login credentials, payment information, or sensitive data.
- Offers that are too good to be true.
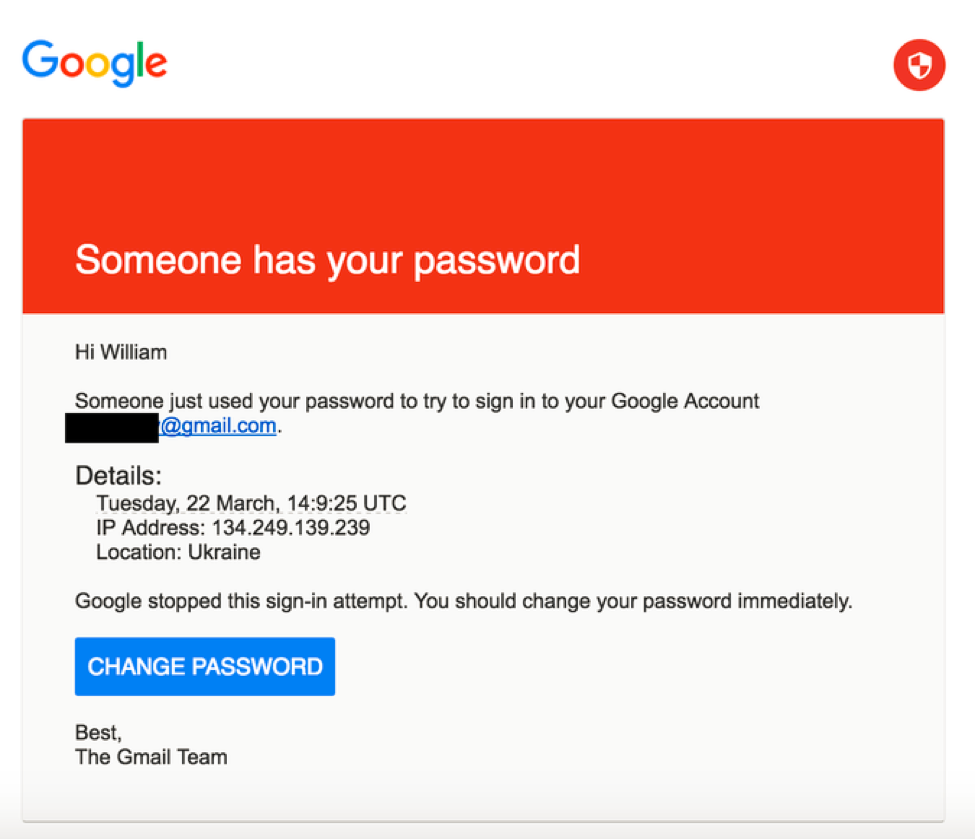
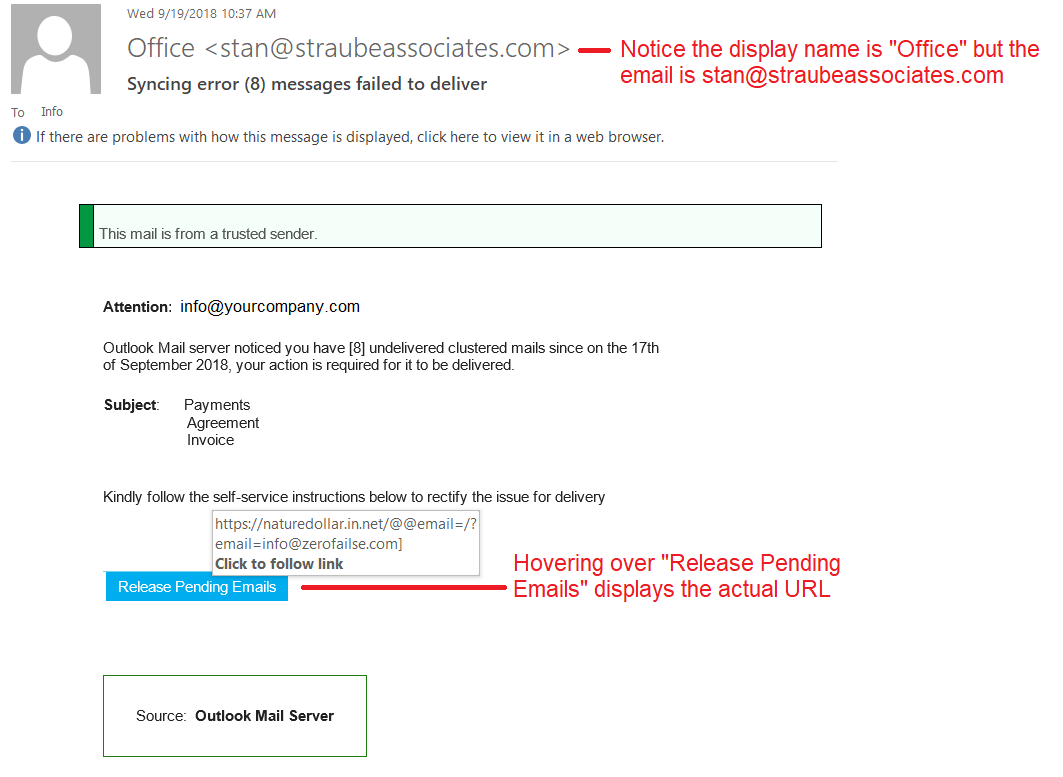
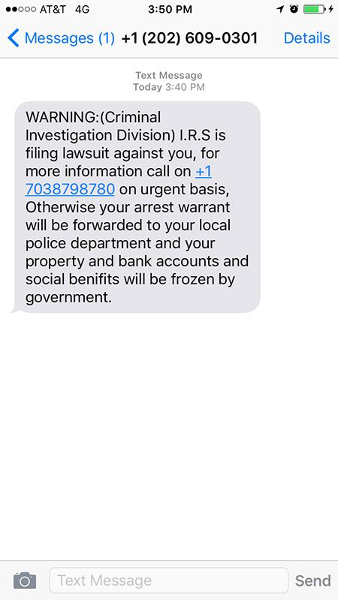
Phishing is also a popular method for cyber attackers to deliver malware by encouraging victims to download a weaponized document or visit a malicious link that will secretly install the malicious payload on the person's computer. These kind of attacks mostly are trying to distribute a trojan malware, ransomware . These cyber hackers are hoping you don't look to deep into the email, that you just gloss over the details and click on the link, or download the attachment. Below is a screenshot of a phishing email, and you can see just how tricky they can be.
Why is Phishing called Phishing?
The overall term for these scams -- Phishing -- is a modified version of the word 'fishing' except in this instance the one doing this fishing is a scammer and they're trying to catch you and reel you in with their sneaky email lure. In most cases, they will send out many of these lures.
FUN FACT! - Why is Phishing spelled with a "Ph"?
The “ph” spelling of phishing is influenced by an earlier word for an illicit act: phreaking, which involves fraudulently using an electronic device to avoid paying for telephone calls. The people who perpetrated phreaking were called “Phreaks,” and since phreaks and hackers were closely linked, the “ph” spelling was used to denote the phishing scams involving these underground groups. Pretty cool!
We hope by sharing these resources with you, that you will have the tools and information necessary to make informed decisions when using the Internet.
Security Awareness Week 2: Ransomware
The CISA defines Ransomware as a "form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption."
Ransomware can be planted into a network using many methods, like Phishing and Social Engineering. Once it is planted, hackers locate and secure access to important files and move those files to a secure network of their own.
Oftentimes, a hacker needs only access into a network, and can gain such access in a myriad of ways. For example:
- By sending phishing emails requesting login information or containing malicious code(as we have seen in last week's post)
- Looking for weaknesses within your network's security
- Users are redirected to a suspicious website that infects their computer by browsing or prompts for them to download files off the internet.
Computer Safety Tips:
Regularly back up important and sensitive data to a separate drive.
Install and regularly update antivirus software on your device.
Exercise caution when following links in emails, text messages, and websites.
Be mindful of what files your are downloading from the internet and avoid suspicious sites.
SPU Employees SPU-Managed Devices:
Software and application patches, anti-virus updates, data backups, mandatory browser and security settings are all implemented by CIS and enforced on your school-issued devices.
However, it is still essential for all employees to use their best judgement when viewing emails and websites.
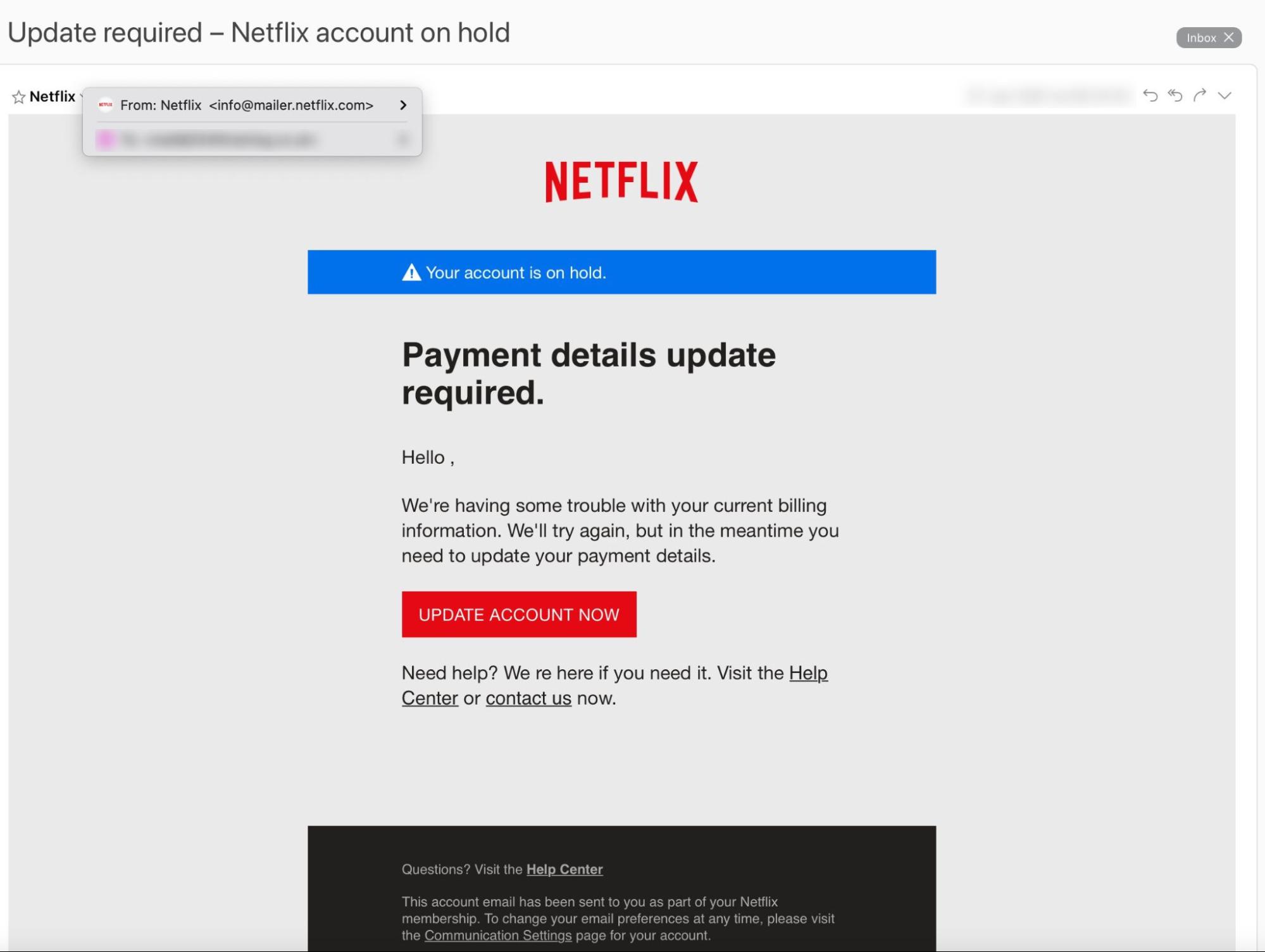
Example 1. Fake websites
A cyber-criminal will design a carefully-worded phishing email which includes a link to a spoofed version of a popular website. The website imitates the layout of the original site to trick the victim into entering their account credentials.
Example 2. CEO Fraud
An attacker will take control of an email address familiar to the employee, such as their company’s CEO, Human Resources Manager, or IT admin. The hacker will assume this individual’s identity and ask the user to complete an urgent action, such as transferring funds, updating their personal information, or installing a new app.
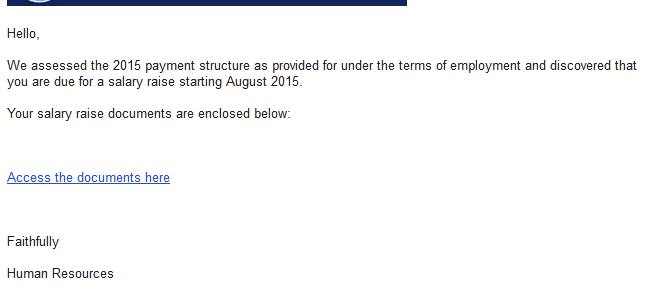
Example 3. Malware
In these types of phishing attacks, an attacker will try to trick an employee into clicking on a malicious email attachment. Usually, this type of attack is carried out with a fake invoice or delivery notification.
If you think that the email may be legit, go to a link that you know is safe (one that you have save for the company) and log in from there. Or, you can always call the company and confirm or deny the validity of the email you received.
REMEMBER
If you don't recognize the sender, NEVER click on the attachments or links!
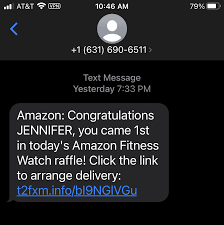
Example 4. Smishing
An SMS-based phishing attack in which a hacker will send an SMS or voice message asking the recipient to click on a link to accept a gift, change your password or call a number. The link will take them to a phishing website that they will use to try and gather more information from you.
Also, the link you click on could have malware in it. What does that mean? It could install a program on your phone that will allow the hacker to gain access to all your personal information, e.g. contacts, passwords, email, photos.
Example 5. Vishing
An unknown caller will call the victim and or leave a voicemail urging them to phone them back and hand over personal information, usually by impersonating someone from a trusted company.
The most common type of this is a Tech Support Call.
This attack is widespread in large companies where employees might not know or have met members of the tech support department. Scammers will pretend they need to do a computer update or repair and ask for the victim’s password to do it.
Education is key to beating these attacks. Frequently remind users that you will never ask them to divulge their password over the phone and that they shouldn’t do so under any circumstance.
Creating a Strong Passphrase
It is also important for users to use a strong Passphrase or password for securing your account. A strong password will protect your account while also not containing any personally identifiable words; like your mother's maiden name or your childhood pet. It is also important to use a strong or complex password, as a more simple passphrase can be easily guessed.
Here are some key things to follow when creating a password:
- Use a combination of numbers, capitalization and special characters.
- Use a longer passphrase that you can easily remember.
- Don't use a password you have used before, or a slight variation of a pre-existing password.
Do NOT write down OR your share your SPU password with anyone.
Password Managing
If you are worried about keeping track of your passwords, use a password manager that will keep track and record all of your passwords and where they are used. It is also likely that your phone or Google account will have password tracking enabled.
For more information on SPU's Password Policies, please select here.
Cybersecurity Awareness Month Quizzes
Thank you for joining us for this year's Cybersecurity Awareness month as we covered Phishing, Ransomware, Social Engineering (Spear Phishing), Passphrases, and Canary Files.
If you have questions or concerns about the topics covered, or would like to learn more, a student technician with the HelpDesk would be more than happy to assist! You can contact the HelpDesk by phone at 206.281.2982 or by email at help@spu.edu.
As a reminder, we are offering one quiz for Faculty and Staff and one quiz for Students to test their knowledge on the topics we covered this month. The quiz will remain open until November 15th, 2023.
A Few Rules to Follow:
- One quiz attempt per individual.
- A student may not take the employee quiz and employees may not take the student quiz.
- Only scores of 100% will be automatically entered into the raffle.
- Prizes will only be given out to the winning individual(s) after they have made their *selection.
- One prize per winner.
*Raffle winners will be contacted by CIS and choose their prize from the available options. Options include bluetooth speakers and/or gift cards.
Faculty and Staff Quiz Here
Student Quiz Here
Is Your Computer Connected to SPU?
CIS works behind the scenes to make sure your SPU-issued Windows computer is updated with the latest security patches, performing optimally, and has access to the SPU Software Center. Device management is crucial in protecting and securing sensitive information, and you can do your part by making sure your SPU computer connects to our management domain.
To ensure your device is secure and connecting properly, please follow the instructions on the Software Center page to load and install an application (we recommend using this time to make sure Zoom is on the current version 5.10.7). If you are unable to load the Software Center or the installation does not succeed, please contact CIS so we can make sure this service, as well as other update services are running correctly on your computer.
Software Updates
Some software tools, such as Zoom, won't work unless you are on the current version. Make sure these tools are updated before you need them in class. If you didn't already install the latest version of Zoom from the Software Center on your computer (see above), do so now and check if other software updates are available.
Office Equipment
Gather any office equipment that you took home for the summer. Possible items may include your computer, monitor(s), docking station, cables, keyboard, mouse, printer, headset, webcam, office chair, etc. Carefully package your equipment when transporting to avoid costly damage.
Please Check Your Classrooms in Advance!
In-Person Classes
Stop by your classroom and log in to the podium computer or try plugging in your laptop if you plan to use it for your lessons to make sure you have the right adaptors. Do a quick run-through of a presentation and test any specialized software. If you spot any problems, please contact the CIS Help Desk at 206-281-2982 or www.spu.edu/cishelpdesk .
If you need a refresher on how to operate the podium PCs or other presenting technologies in classrooms, please first refer to the recorded lesson on SPU Classroom Technology . To schedule a one-on-one training with a CIS technician, please contact the CIS HelpDesk at 206-281-2982 or www.spu.edu/cishelpdesk.
If you might need to record or stream your in-person class to support a student not able to be in the room, please test your webcam and microphone with the computer in the classroom (or be prepared to bring your laptop). If you have any questions about recording with Zoom or Panopto, sharing the recording with your class, or need a webcam and microphone please contact Educational Technology and Media at etmhelp@spu.edu for advice as soon as possible.
Please do not unplug, power off equipment, or move computer podium cables. Before leaving your classroom please return the podium equipment exactly how you found it.
Online Classes
If you will teach online, please ensure you have a Canvas course set up. If you are teaching synchronously, please also familiarize yourself with setting up a Zoom class and make sure Zoom is updated to the latest version. Start here for information about features available on Zoom and how to get signed up. A Zoom Licensed account should be used for any class instruction. This will allow you to host a class over Zoom class of unlimited duration and with up to 300 participants.
Can I Have a Mac?
Yes! If you or your instruction would benefit from using a Apple Mac instead of a standard PC you may select one at your next upgrade cycle. Some Mac options may have an additional fee due to higher cost. See the Centralized PC Purchasing Policy for details.
Protecting Student Privacy
We all value our privacy and are frustrated when others are careless with the sensitive information we entrust them with. You are entrusted with sensitive information about students and others the Seattle Pacific University community and you share in the responsibility to protect our students by complying with regulations and University policies. The Regulated Data Chart provides a simple overview of which places have the security and contractual protections to store certain types of sensitive Regulated Data. You can also learn more about campus Data Policy, Data Laws and Regulations, and Handling Confidential Data responsibly.
Using a Personal Computer for Work
Personal computers and departmentally-purchased computers (unmanaged) do not have the same security and regulatory compliance protections that SPU-managed computers purchased and managed by CIS have. Personal devices or cloud resources (Google Docs, DropBox, etc.) used for work purposes are subject to eDiscovery and can be confiscated or seized if they are suspected to contain information related to a lawsuit against the institution. Protect our student's data, yourself, your property, and the University by following the Use of Personal / Un-Managed Devices for Work policy.
Use OneDrive for Cloud File Storage
Storage platforms like Dropbox and Google Drive are not compliant for sensitive or regulated University data, such as information protect by FERPA. OneDrive for Business is the contractually protected platform approved for storing sensitive documents in the cloud.
CIS Staffing Shortage
Like many administrative offices, CIS continues to experience staffing shortages. The dedicated folks in CIS thank you in advance for your patience as we churn through your support requests at a slower pace than either of us would like. If you know someone who would be a good addition to the CIS team, the department is offering a $1000 referral bonus for hires that retain for at least 6 months.
Classrooms and Technology
Demaray Hall 150 received a significant upgrade this summer, including a brand new projector, ceiling mounted speakers, an iPad for secondary room controls, microphones and more. This will help the room be more user friendly and set us up for other future enhancements in the space. We are also beginning to make plans now for additional room updates over Winter break.
SPU Classroom Technology Training
CIS has published various technology training videos including one co-hosted with ETM on Classroom Technology. You can find this and other recordings here .
Subjects covered specifically in the SPU Classroom Technology video are:
- 00:00-25:45 - review of existing technology in classrooms (computer podium, projector controls, document camera), troubleshooting potential technology issues
- 25:45-38:00 - recording lessons in an on-campus classroom (Panopto), hardware needed to record, recording challenges in the classroom
You are welcome to live stream from the classroom, however live streaming in classrooms is currently not supported by CIS or ETM.
Emergency Classroom Support
Even with good preparation it is always possible that some technology will not function as expected in the classroom. It is CIS's priority to assist you in these cases.
If you run into technology problems in your classroom, call the CIS HelpDesk at 206-281-2982. We will do everything we can to provide assistance on the phone or immediately dispatch a technician to your room.
Our goal is to correct technology issues before they turn into a classroom crisis. If you experience any trouble at all during a class period but can't wait for support, please be sure and let us know about it later.
Software in Classrooms and Academic Labs
All classroom and lab computers have a broad range of software installed and configured, but please let the CIS HelpDesk know if anything is missing. Additionally, if there are any new software needs, please inform the CIS HelpDesk as soon as possible. There is often a review and testing process required for new software.
For more information on how to request new software for academic computers or how to request an update to existing software, see here .
Peer-to-Peer File Sharing and Copyright Compliance
File sharing software that copies and distributes songs, movies, videos, games, and software applications without the permission of the owner is a Copyright Law violation that can subject you to criminal and civil liability. Content owners use technological means to track the file sharing of their intellectual property on the Internet. SPU is required by law to inform you if we are aware, you have violated copyright law and must provide your information to copyright owners for legal action if you do not cease illegal activity. You are responsible for the activities of your computer when connected to the campus network. See Copyright Basics and DMCA Copyright Compliance / Peer-to-Peer File Sharing for more information about copyright compliance.