Restricted Files on Matthew
Overview
As a crucial step in ransomware prevention, SPU now blocks specific executable file types and suspicious file naming patterns from being written to DFS Depts shares without prior review.
We understand that there are limited but legitimate business cases where files of these extensions need to be saved to a shared folder. Please contact the CIS Help Desk if you are still stuck after reading below.
What will I see?
If you experience or receive a similar to the message to either image below, and you believe it is in error, please contact the CIS HelpDesk so your file(s) can be evaluated.
When saving a file to Matthew, you may experience the following:
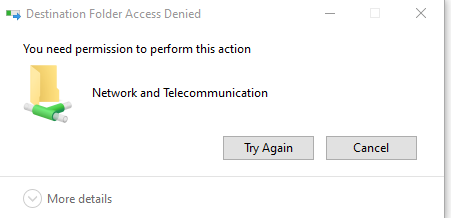
or receive an email like the one below:
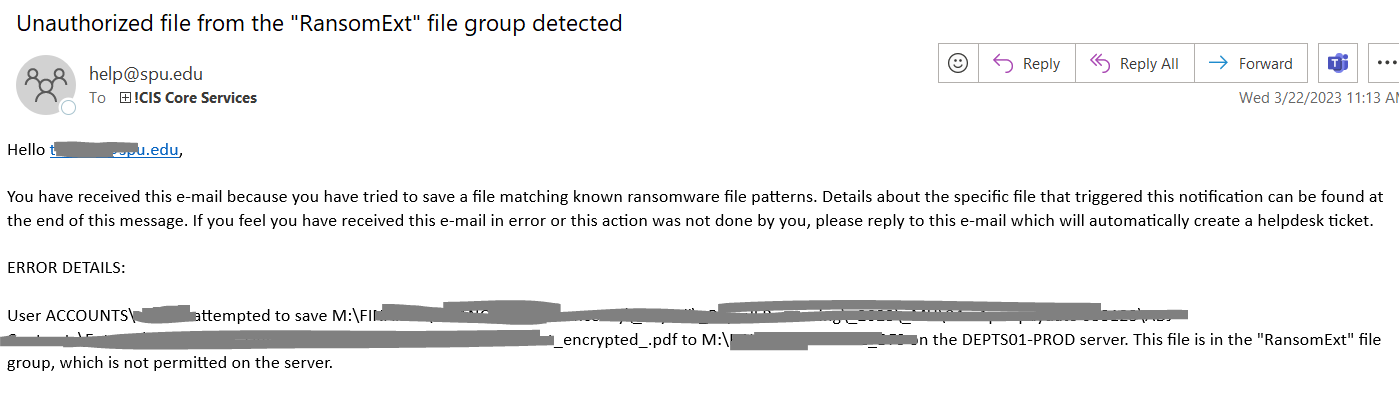
Examples of Blocked File Extensions
Below are some examples of file extensions that are not permitted to be saved by the general user community on departmental file shares:
|
|
|
|---|
If you do not see file extensions when looking at your Documents, you may need to adjust your computer settings to show file extensions.
Examples of Blocked File Naming Patterns
In addition to executables, we also block the writing of files with highly suspect naming patterns often found in ransomware. File names and file paths that include multiple periods or words such as "encrypt" or "crypt4" will automatically be blocked. If you get blocked from saving what you believe to be a good file, consider simplifying the name by eliminating special characters or suspect wording.
Related articles
-
Page:
-
Page:
-
Page:
-
Page:
-
Page: