CIS Security Notices
October is Cybersecurity Awareness Month - CSA
It is CIS's responsibility to share some vital information about how to be safe while using the internet and managing yours and students' information.
Over the next few weeks, CIS will be releasing a weekly blog post that expands on four core topics for this year's CSA month: Phishing, Social Engineering (whaling), Passphrases for passwords, and Ransomware.
At the end of the month, there will be a quiz released to employees and students. Receiving 100% on the quiz will automatically enter the user into a raffle. The raffle will have two winners, one student and one employee, who will each receive a prize* from CIS!
Keep an eye out for the first blog post on October 9, and then every following Monday until the end of the month!
*Please note that prizes will be ordered once they are selected by the prize-winners. CIS will contact prize-winners when the prizes are ready to be picked up from the HelpDesk.
Security Awareness Week 1: Phishing emails
What is Phishing?
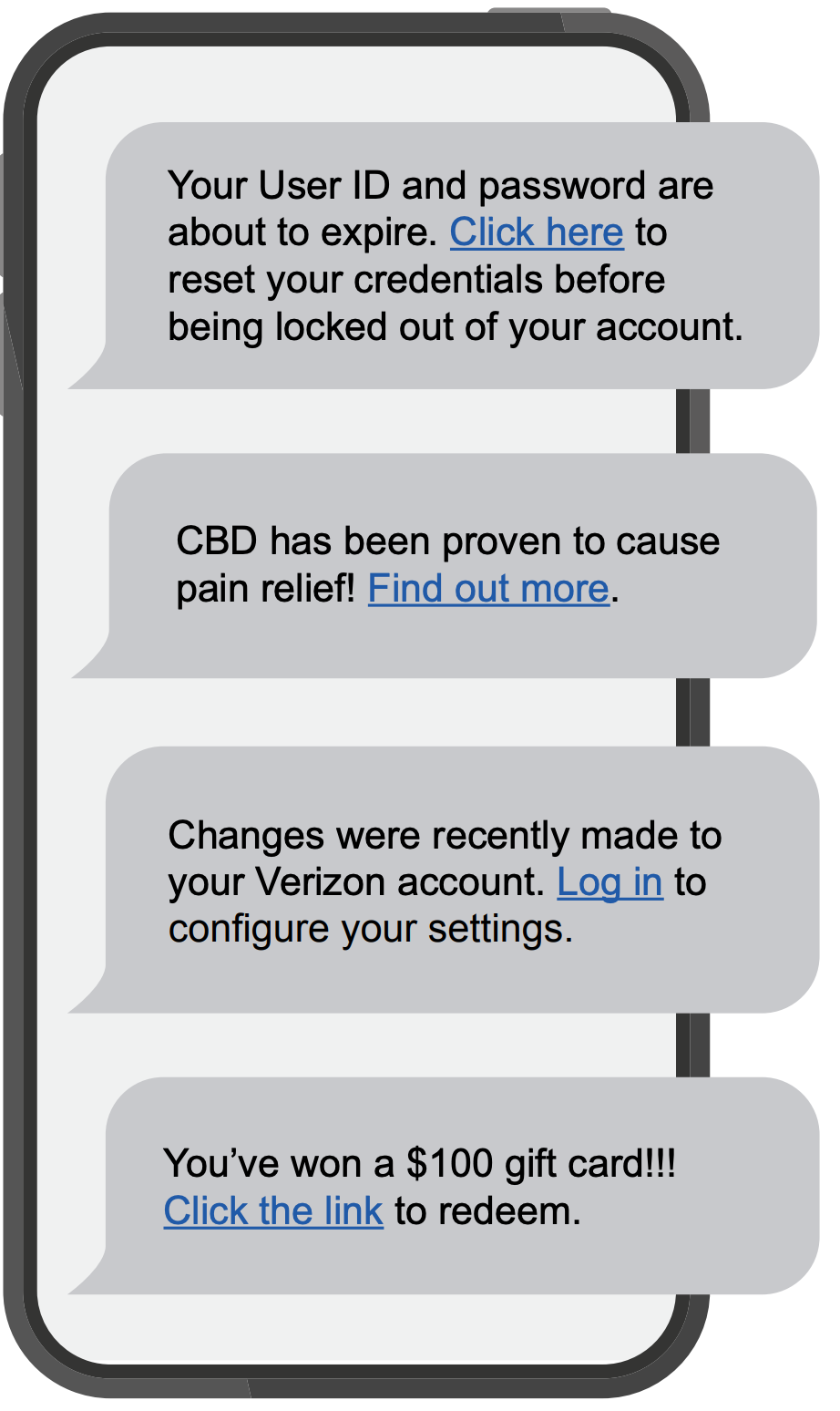
Often carried out over email -- although the scam has now spread beyond suspicious emails to phone calls (so-called "vishing"), social media, SMS messaging services (aka "smishing"), and apps -- a basic Phishing attack attempts to trick the target into doing what the scammer wants.
Exactly what the scammer wants can vary wildly between attacks. It might be handing over passwords to make it easier to hack a company or person, or sending payments to fraudsters instead of the correct account. This information is often stolen by making requests that look entirely legitimate -- like an email from your boss, so you don't think twice about doing what is asked.
How would you identify a Phishing email?
Emails that contain the following should be approached with extreme caution, as these are common traits of phishing email:
- Urgent action demands.
- Multiple sources in the from email address line.
- Poor grammar and spelling errors.
- An unfamiliar greeting or salutation.
- Requests for login credentials, payment information, or sensitive data.
- Offers that are too good to be true.
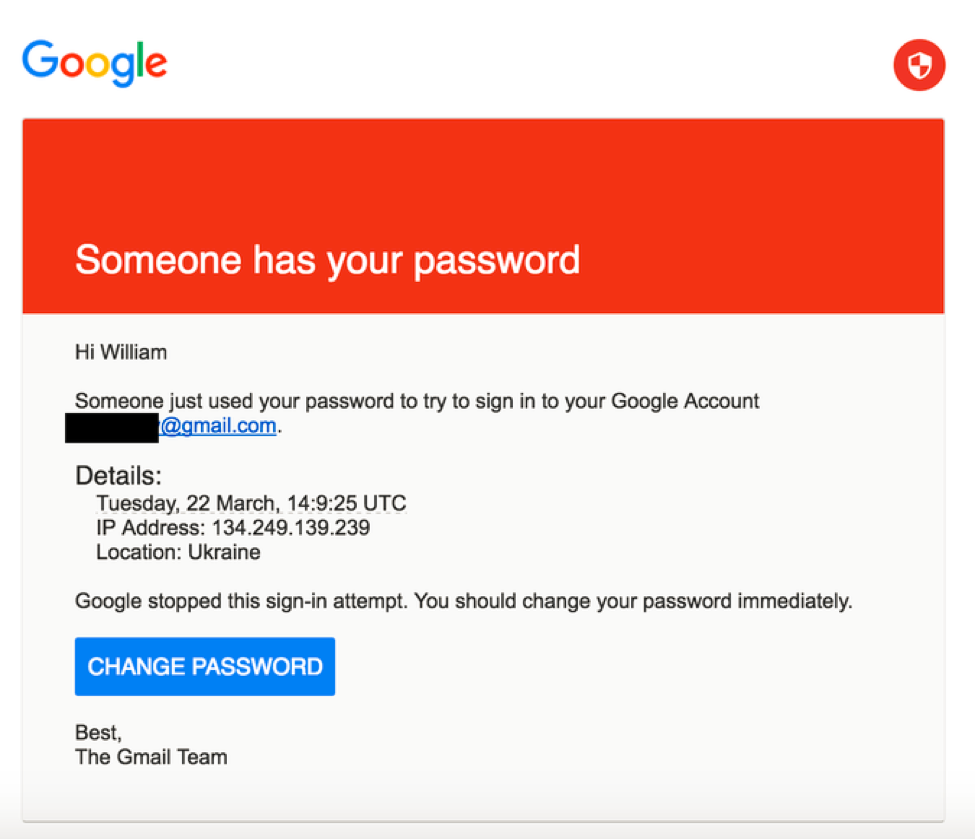
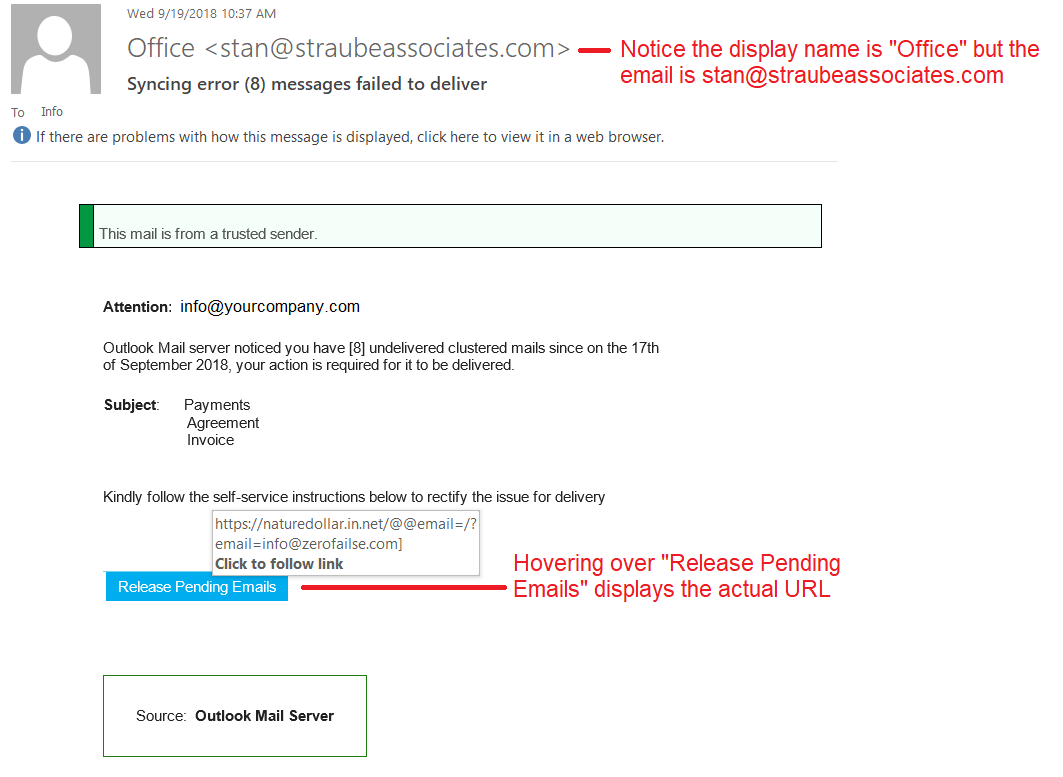
Phishing is also a popular method for cyber attackers to deliver malware by encouraging victims to download a weaponized document or visit a malicious link that will secretly install the malicious payload on the person's computer. These kind of attacks mostly are trying to distribute a trojan malware, ransomware . These cyber hackers are hoping you don't look to deep into the email, that you just gloss over the details and click on the link, or download the attachment. Below is a screenshot of a phishing email, and you can see just how tricky they can be.
Why is Phishing called Phishing?
The overall term for these scams -- Phishing -- is a modified version of the word 'fishing' except in this instance the one doing this fishing is a scammer and they're trying to catch you and reel you in with their sneaky email lure. In most cases, they will send out many of these lures.
FUN FACT! - Why is Phishing spelled with a "Ph"?
The “ph” spelling of phishing is influenced by an earlier word for an illicit act: phreaking, which involves fraudulently using an electronic device to avoid paying for telephone calls. The people who perpetrated phreaking were called “Phreaks,” and since phreaks and hackers were closely linked, the “ph” spelling was used to denote the phishing scams involving these underground groups. Pretty cool!
We hope by sharing these resources with you, that you will have the tools and information necessary to make informed decisions when using the Internet.
Security Awareness Week 2: Ransomware
The CISA defines Ransomware as a "form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption."
Ransomware can be planted into a network using many methods, like Phishing and Social Engineering. Once it is planted, hackers locate and secure access to important files and move those files to a secure network of their own.
Oftentimes, a hacker needs only access into a network, and can gain such access in a myriad of ways. For example:
- By sending phishing emails requesting login information or containing malicious code(as we have seen in last week's post)
- Looking for weaknesses within your network's security
- Users are redirected to a suspicious website that infects their computer by browsing or prompts for them to download files off the internet.
Computer Safety Tips:
Regularly back up important and sensitive data to a separate drive.
Install and regularly update antivirus software on your device.
Exercise caution when following links in emails, text messages, and websites.
Be mindful of what files your are downloading from the internet and avoid suspicious sites.
SPU Employees SPU-Managed Devices:
Software and application patches, anti-virus updates, data backups, mandatory browser and security settings are all implemented by CIS and enforced on your school-issued devices.
However, it is still essential for all employees to use their best judgement when viewing emails and websites.
Example 1. Fake websites
A cyber-criminal will design a carefully-worded phishing email which includes a link to a spoofed version of a popular website. The website imitates the layout of the original site to trick the victim into entering their account credentials.
Example 2. CEO Fraud
An attacker will take control of an email address familiar to the employee, such as their company’s CEO, Human Resources Manager, or IT admin. The hacker will assume this individual’s identity and ask the user to complete an urgent action, such as transferring funds, updating their personal information, or installing a new app.
Example 3. Malware
In these types of phishing attacks, an attacker will try to trick an employee into clicking on a malicious email attachment. Usually, this type of attack is carried out with a fake invoice or delivery notification.
If you think that the email may be legit, go to a link that you know is safe (one that you have save for the company) and log in from there. Or, you can always call the company and confirm or deny the validity of the email you received.
REMEMBER
If you don't recognize the sender, NEVER click on the attachments or links!
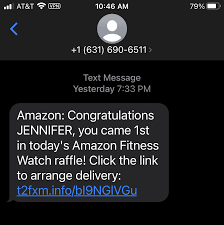
Example 4. Smishing
An SMS-based phishing attack in which a hacker will send an SMS or voice message asking the recipient to click on a link to accept a gift, change your password or call a number. The link will take them to a phishing website that they will use to try and gather more information from you.
Also, the link you click on could have malware in it. What does that mean? It could install a program on your phone that will allow the hacker to gain access to all your personal information, e.g. contacts, passwords, email, photos.
Example 5. Vishing
An unknown caller will call the victim and or leave a voicemail urging them to phone them back and hand over personal information, usually by impersonating someone from a trusted company.
The most common type of this is a Tech Support Call.
This attack is widespread in large companies where employees might not know or have met members of the tech support department. Scammers will pretend they need to do a computer update or repair and ask for the victim’s password to do it.
Education is key to beating these attacks. Frequently remind users that you will never ask them to divulge their password over the phone and that they shouldn’t do so under any circumstance.
Creating a Strong Passphrase
It is also important for users to use a strong Passphrase or password for securing your account. A strong password will protect your account while also not containing any personally identifiable words; like your mother's maiden name or your childhood pet. It is also important to use a strong or complex password, as a more simple passphrase can be easily guessed.
Here are some key things to follow when creating a password:
- Use a combination of numbers, capitalization and special characters.
- Use a longer passphrase that you can easily remember.
- Don't use a password you have used before, or a slight variation of a pre-existing password.
Do NOT write down OR your share your SPU password with anyone.
Password Managing
If you are worried about keeping track of your passwords, use a password manager that will keep track and record all of your passwords and where they are used. It is also likely that your phone or Google account will have password tracking enabled.
For more information on SPU's Password Policies, please select here.
Cybersecurity Awareness Month Quizzes
Thank you for joining us for this year's Cybersecurity Awareness month as we covered Phishing, Ransomware, Social Engineering (Spear Phishing), Passphrases, and Canary Files.
If you have questions or concerns about the topics covered, or would like to learn more, a student technician with the HelpDesk would be more than happy to assist! You can contact the HelpDesk by phone at 206.281.2982 or by email at help@spu.edu.
As a reminder, we are offering one quiz for Faculty and Staff and one quiz for Students to test their knowledge on the topics we covered this month. The quiz will remain open until November 15th, 2023.
A Few Rules to Follow:
- One quiz attempt per individual.
- A student may not take the employee quiz and employees may not take the student quiz.
- Only scores of 100% will be automatically entered into the raffle.
- Prizes will only be given out to the winning individual(s) after they have made their *selection.
- One prize per winner.
*Raffle winners will be contacted by CIS and choose their prize from the available options. Options include bluetooth speakers and/or gift cards.
Faculty and Staff Quiz Here
Student Quiz Here
Multifactor Authentication Everywhere
Whether it's as a part of your SPU account or your bank account, Multi-factor Authentication (MFA) is here to stay. While it's not a silver bullet against all cybersecurity threats (and we still need to be on the watch for "phishy" behavior), it's a simple measure that should be enabled anywhere it is available.
Multi-factor Authentication is a process by which you use a second "factor" to login to an online account, in addition to the username and password you already know. This second factor is most often "something you have", and can be a device with a registered application, a phone number to receive calls or texts, or a dedicated security token that generates an authentication code.
SPU is finishing up its migration of all "@spu.edu" accounts to MFA this Fall using Azure MFA (if you haven't enrolled already, do so now!). This means that all logins used to access SPU systems will be afforded this protection and our accounts and systems will be more secure. Importantly, this will also help prevent bad actors from using a compromised account to bombard campus inboxes with phishing or scamming attempts.
Do your part and set up MFA both here at SPU and anywhere else you have the option of doing so!
Getting set up with a Password Manager
Last week we talked about the importance of using Multi-factor Authentication Everywhere and how it can help protect you against cybersecurity threats. This week we’re focused on your password and how you can protect yourself by setting up a Password Manager!
Most people tend to use easy to remember passwords, but those are also easily guessed and are thus weak to cyber-attacks. If you use the same password for your email, bank, social media, and healthcare accounts, an identity thief who found your login info on the dark web would be able to access all kinds of sensitive information with a single username and password.
What are the Benefits of a Password Manager?
Individuals and businesses may find password managers useful in several circumstances:
- They can generate secure passwords for you.
Many password managers will prompt you with an automatically generated secure password whenever you create a new account through an app or website. These passwords tend to be long blends of letters, numbers, and special characters. If you opt to use a suggested password, the manager will automatically store it for you. - They can save time. While keeping all your login information safe is certainly a plus, a password manager can also store and auto-fill information like your address, phone number, and credit card. Online shopping just got a lot easier!
- They protect your identity. If a criminal can guess one of your passwords, they’ll try to access more of your accounts by trying that same password in other commonly used websites. But if you’re using unique passwords, they may not be able to gain access to your other accounts. While a password manager isn’t foolproof, it does provide an extra layer of security.
- They can let you know about phishing sites. Phishing and spear phishing websites are scams that spoof legitimate websites. While they may look like the real deal, their goal is to steal your login information and commit fraud. A password manager can offer protection from phishing sites because each username and password is tied to a specific URL. Even if you visit a phishing site, your login information won’t autofill because the URL doesn’t match the one saved in the password manager. This might give you pause before you enter your personal information and keep a criminal from stealing your personal information.
Apart from using a service or app to manage your login information, other steps that you can take to keep your information safe include not reusing passwords and creating strong, unique passwords for each website or application you log into.
What password manager should I adopt?
There are many password managers to choose from, how do I pick a good one? Checking reviews from reputable sources, like Wired or CNET will help you identify a password manager that will meet your needs. Some commonly used Password Managers are: 1Password, Bitwarden, LastPass, and many others.
Additional Resources
Looking for more information about how password managers work? Check out the following resources.
Colby, C., Hodge, R., Tomascheck, A., October 2022. Best password manager to use for 2022. https://www.cnet.com/tech/services-and-software/best-password-manager/. Retrieved October, 2022.
Gilbertson, S. August 2022. The best password managers to secure your digital life. Wired. https://www.wired.com/story/best-password-managers/. Retrieved on October, 2022.
National Cybersecurity Alliance. May 2022. Online safety + Privacy basics: Passwords. https://staysafeonline.org/online-safety-privacy-basics/passwords-securing-accounts/. Retrieved October 2022.
National Cybersecurity Alliance. September 2022. Online safety + Privacy basics: Password managers. https://staysafeonline.org/online-safety-privacy-basics/password-managers/. Retrieved October 2022.
Identifying Malicious Emails
If you’ve been following along with our weekly Cybersecurity Awareness posts, by now you have MFA enabled on your accounts and a password manager set up to store all your passwords. Those tools help to secure your account, but malicious actors have other ways to steal data or defraud users.
Since the start of October, Microsoft has flagged 125,766 emails sent to SPU addresses as either phishing attempts, fraud, or malware. Can you distinguish between the different types?
- Phishing emails attempt to steal your account credentials.
- Fraud emails attempt to steal money from you. These can be emails such as:
- Requests gift cards that will be “paid back right away”
- Help wanted postings that require you to send money before they can hire you
- Malware emails contain attachments that install malicious programs on your system when opened.
The large majority of attempts like those mentioned above are automatically blocked by safeguards CIS has implemented in SPU’s systems. But for those that make it through, here are some steps you can take to protect yourself:
- Take a few seconds to reread and review the email (answering yes to any of the following questions increases the chances the email is a phishing attempt).
- Is the offer too good to be true?
- Is the sender asking you to send them personal information and/or money?
- Is the language urgent or threatening permanent loss of access?
- Is the greeting generic or ambiguous?
- Is the request in the email a strange business request, especially from that particular sender?
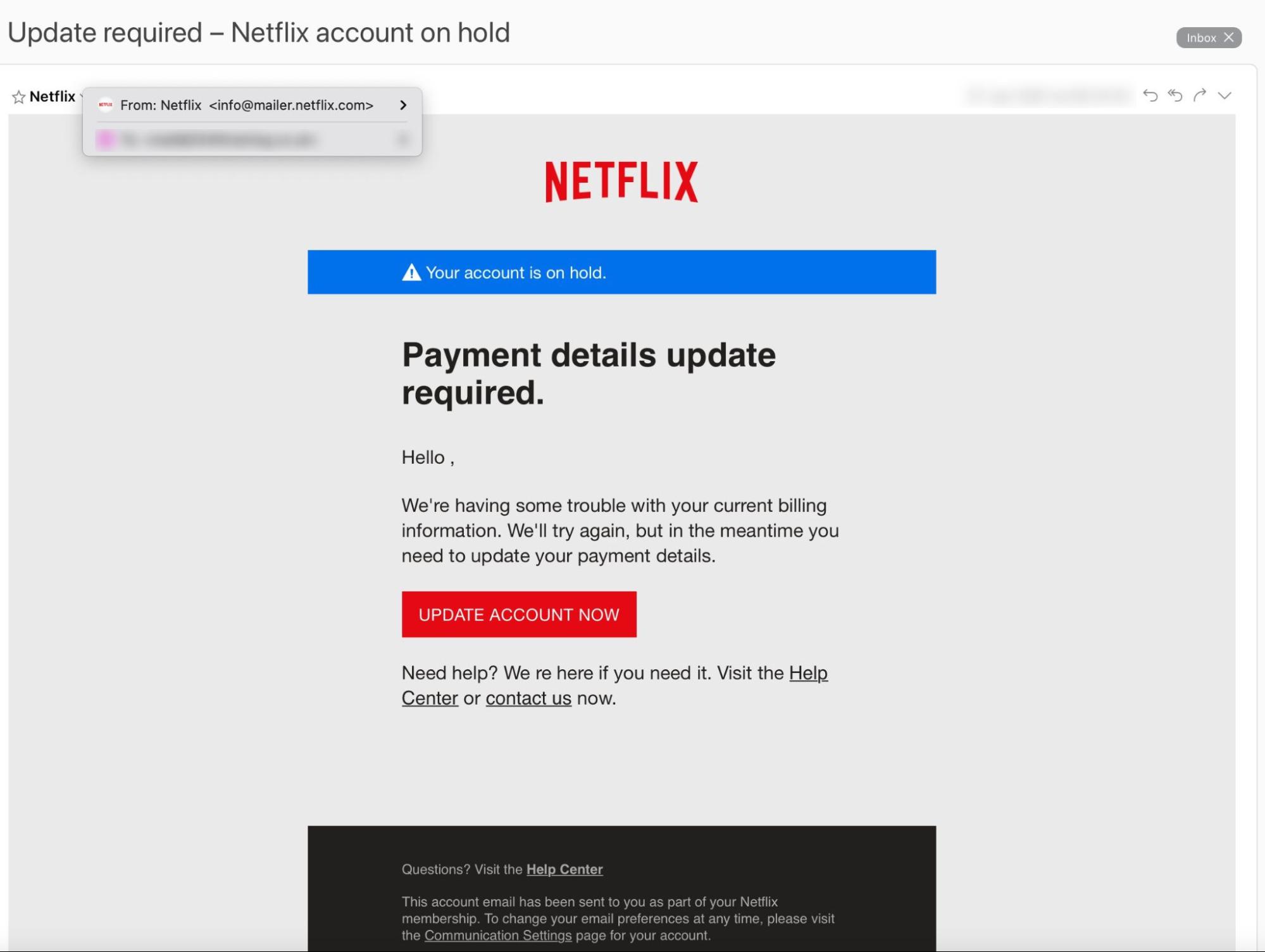
- Confirm the sender of the email.
- Hover over the display name of the email to review the address from which it was sent. Does the address match the supposed sender of the email?
- Beware of email addresses that are very similar looking to valid addresses such as: pavpal.com vs paypal.com or anazon.com vs amazon.com
- Never click links in suspicious emails.
- Never use a link in the email to contact the sender. Call them using contact information on their website instead, to confirm whether or not the emailed request is valid.
- Don’t open attachments from non-trusted senders.
- Opening attachments risks installing malware on your computer. Once installed, the malware can quickly propagate out to other areas of our network and infect the entire system.
- Contact CIS if you still have questions.
- If you receive an email that passes all of the above checks but still seems suspect to you, contact CIS (help@spu.edu) and ask us to review it. We have additional tools and resources we can use to attempt to confirm its validity.
Managing your Software
In our last installment for Cybersecurity Awareness, we’re focusing on software updates. Often, when we think about software updates, we think about our computer and our phone, but there’s more to updates than just those devices.
The key things to remember about software updates are:
- Update often
New patches come out on a regular basis and there will be new vulnerabilities. The longer you wait, the more vulnerable you and your data are to bad actors. - Automate it whenever possible
With the number of devices and applications out there that we each use, it can be hard to keep track of updates. This is where automation comes into play. Sometimes, your devices and applications can keep themselves updated, taking some of the burden off you to remember to do this. - Replace or upgrade unsupported software and hardware
Hardware and/or software that is no longer supported and receiving updates can be problematic because there won’t be patches to protect the system and your information from new attacks and vulnerabilities. Where possible, upgrade or stop connecting the older devices to the internet to keep yourself and your data safe. - Every device that connects to the internet should be updated.
This includes your home router, smart devices used at home like security cameras and doorbells, Bluetooth deadbolt setups, car software, TV’s and more! If your system is online, we recommend keeping up with the updates!
We’re at the end of Cybersecurity Awareness month, but we hope by sharing these resources with you, that you will have the tools and information necessary to make informed decisions when using the Internet.
As part of our ongoing efforts to better protect campus and reduce administrative costs, CIS has licensed Microsoft's Azure Multi-Factor Authentication (MFA) for all current Duo 2FA users and all Students at a lower cost than our current Employee-only coverage through Duo.
Extending this service to campus is both a best practice and will greatly reduce the number of compromised SPU student accounts, consequently decreasing the number of phishing emails sent to others from within the SPU community.
Migration Timeline
- Pilot (Jan-Apr): CIS staff and several dozen pilot-users from around campus have already migrated to Azure MFA and have been using it to login to campus systems since as early as January 2022.
- Current User Opt-in (April 18): Starting today all current Duo Users are eligible to migrate to Azure MFA at a time convenient to them.
Instructions on how to enroll can be found here: Enrolling In Azure MFA.
- Current User Migration Deadlines (April 25-May 27): Starting next week all users that have not yet migrated will begin to be placed in a phased migration cohort. Each cohort will have two weeks to migrate before being required to do so. As soon as you are placed in a cohort you will begin to see a notification reminding you of your deadline for migrating each time you log in to an online SPU system.
- Current & Incoming Students (Summer/Fall 2022): Migration of the general student body will begin as an opt-in process around the start of Summer Quarter (for all current and incoming students) and we aim to conclude setup of all students in the weeks following the start of Fall Quarter. Many current students will already have this protection by virtue of being a Student Employee.
- Alumni and other populations (Summer/Fall 2022): Migration of other accounts to Azure MFA will take place during Summer and Fall, with all accounts being migrated prior to the end of 2022.
Azure Multi-Factor Authentication (MFA)
Multi-factor authentication has been in use at SPU since 2018 and adds the requirement of having "something you have" (e.g.: a registered phone), in addition to "something you know" (e.g.: SPU username and password) in order to login to your SPU account. This added layer of protection ensures that even if an account credential is compromised, a malicious actor cannot gain access to your SPU account without both authentication factors, and your access to sensitive student data as well as any personal data is safeguarded. Since rolling this service out to campus employees, we've had zero compromised accounts among those users.
Azure MFA is the MFA service offered by Microsoft and is part of our ongoing campus license to Microsoft 365 online services. By tying our MFA provider in with our campus licensing, we are able to provide this protection to all campus user accounts and reduce the number of systems SPU uses.
The primary authentication method recommended is the Authenticator App available on Android and Apple devices. This simple app allows you easily authenticate a login by pushing a notification to your device each time you log in to an SPU service from a new device or internet browser.
Podium Retirement
Effective this morning, the "podium" login account has been retired from use at SPU. This was an account primarily used by external and conference guests to present content on SPU-managed devices, but some employees have used it for non-sensitive tasks on SPU-managed devices as well. With the advent of Azure MFA, use of this account (in conjunction with accessing SPU services) could result in a security hole for that user's account. As such, this account needs to be officially retired. If you are aware of any user that previously used this account, please let them know that they will need to login with their SPU credential on all campus systems. If you are working with an external group that needs access to an SPU-managed workstation, please contact the CIS HelpDesk for assistance.
The last 2 years have seen a dramatic increase in cybercrime. From 2019 to 2020, there was a 435% increase in ransomware attacks, digital attacks aimed at stealing private data and holding it for ransom. 80% of these attacks used fake emails, known as phishing, to trick people into giving up their personal information. Here at home, SPU students are scammed out of thousands of dollars every year by online scams and fraud. How can you protect yourself? Learn best practices for staying safe online to protect yourself and your wallet. For more information visit StaySafeOnline.org
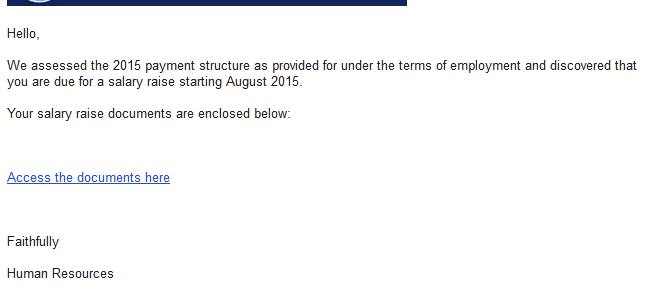
Job Scams
Occasionally you may receive an email scam offering an employment opportunity from someone who appears to be associated with SPU. Please delete these messages and do not respond. All legitimate jobs at the university are posted on SPU's Handshake platform . Employers on Handshake are vetted to guarantee their trustworthiness. Here is a blog post with more information to help you identify and avoid employment scammers. If you have any questions about the legitimacy of an email message please forward it to help@spu.edu. NEVER purchase gift cards or provide your banking information before confirming a job is legitimate.
Phishing
Phishing scams often come in the form of email messages attempting to steal your username and password. DO NOT reply to these messages or follow web links where you must confirm or enter your username and password. If you have questions about the legitimacy of a message, trust your instincts and proceed with heightened caution. Most "account alerts" are not only sent via email but posted within your account settings/messages of the secure web site in question. If possible, navigate directly to your account through a secure web connection (https:) to verify the legitimacy of account alerts. And remember - we are here to help! If you ever have any question as to the legitimacy of an email, the please forward it to help@spu.edu for assessment. See last year's Cybersecurity Awareness Month blog post about phishing for additional information.
Protect Your Password
SPU will NEVER ask you to send or verify your login credentials or other personal/confidential information via email. Your account credentials should not be shared with anyone! Learn Password Best Practices.
Share With Care
Assume that any information you enter online is public unless you are using a known, trusted, secure site. Be careful when posting to social networking sites (Facebook, Twitter, etc.), personal web pages, and blogs since these are great places for people to find personal information about you for identity theft. Once you post something, you can't take it back!
A good rule is to only post information you would be willing to put on a banner in a public place.
Back it Up
Protect your valuable work, music, photos and other digital information by making an electronic copy and storing it safely. If you have a copy of your data and your device falls victim to ransomware or other cyber threats, you will be able to restore the data from a backup. Use the 3-2-1 rule as a guide to backing up your data. The rule is: keep at least three (3) copies of your data, and store two (2) backup copies on different storage media, with one (1) of them stored at another location.
Keep a Clean Machine
Keep all software on internet connecting devices – including personal computers, smartphones and tablets – current to reduce risk of infection from ransomware and malware. Configure your devices to automatically update or to notify you when an update is available to ensure you always have the latest security updates protecting you.
The year 2020 broke all the records when it came to cybersecurity incidents. Driven by the pandemic and the shift to remote work, there were over 1.4M reports of identity theft in the US, more than double the reported count in 2019. Malware increased by more than 350% and several colleges and universities have been significantly impacted by ransomware. The higher education industry is particularly vulnerable as it holds tremendous amounts of data about its constituents and is generally considered a "soft target" (easy to attack). SPU is not immune to these incidents as the University continues to block millions of attacks per day and combat fraudsters impersonating SPU deans and administrators. The University strives to be diligent about security to protect the SPU community and we need your help!
Change on the Horizon
The rise of incidents has prompted a reciprocal increase in SPU's cybersecurity insurance. The Department of Education has also taken notice and is contemplating a shift from merely recommending NIST 800-171 cybersecurity standards to requiring institutions to meet them. There are also new requirements for institutions accepting federal financial aid under CUI and GLBA. The Office of Computer and Information Systems, in partnership with the Office of Risk Management, are working to adapt SPU policies, training programs, and systems to reduce risk and protect the SPU community and our students. While some changes are necessary, SPU will endeavor to keep them from impacting your important work. The following are some of the changes approved by the Senior Leadership Council that are coming in the near term.
Cybersecurity Training
There is a new Cybersecurity and Online Habits training available for you to take as part of the Human Resources compliance training program. Both the Gramm-Leach-Bliley Act and the NIST 800-171 require SPU to have a mandatory cybersecurity training that is used in employee onboarding and repeated annually. Training is also strongly recommended by SPUs cybersecurity insurance provider. This applies to all faculty, staff, and student employees. Please complete this training by January 1, 2022.
For a more humorous take on cybersecurity issues, see the videos in last year's cybersecurity awareness month blog post.
Email Data Loss Prevention
Email is not a secure medium and is not safe for transmitting sensitive information. SPU will begin rolling out a new feature called Email Data Loss Prevention (DLP) that will identify sensitive data that should not be sent via email. During the rollout period, you will see a security warning before you send a message containing sensitive information, and you will be allowed to override the DLP system. If you get this warning during a normal business process, please request a Business Process Consultation to help you transition to a more secure way of sending or receiving sensitive information. After the rollout period, the Email DLP system will block any emails containing sensitive data and you will not be able to override it.
Vendor Cybersecurity Assessments
Completing a Higher Education Community Vendor Assessment Toolkit (HECVAT) assessment is now required for all new vendors that have a software component and is recommended for vendors that are only providing services, but have access to SPU Data. This includes cloud or SaaS vendors as well as hardware and equipment vendors that include a software component (for example a new HVAC system able to be remotely managed by computer). This change has been noted in the Enterprise Software Acquisition policy and is required by the Gramm-Leach-Bliley Act and by NIST 800-171.
Protecting Student Privacy
Everyone values privacy and is frustrated when companies are careless with the sensitive information they're entrusted with. As a member of the Seattle Pacific University community, you share in the responsibility to protect our students by complying with data security regulations and University policies. The Regulated Data Chart provides a simple overview of which places have the security and contractual protections to store certain types of sensitive Regulated Data. You can also learn more about campus Data Policy, Data Laws and Regulations, and Handling Confidential Data responsibly.
Using a Personal Computer for Work
Personal computers and departmentally-purchased computers (unmanaged) do not have the same security and regulatory compliance protections that SPU-managed computers purchased and managed by CIS have. Personal devices or cloud resources (like Google Docs) used for work purposes are subject to eDiscovery and can be confiscated or seized if they are suspected to contain information related to a lawsuit against the institution. Protect yourself, your property, and the University by following the Use of Personal / Un-Managed Devices for Work policy.
Use OneDrive for Cloud File Storage
Storage platforms like Dropbox and Google Drive are not compliant for sensitive or regulated University data, such as information protect by FERPA. OneDrive for Business, along with Microsoft Teams and SharePoint, are the contractually protected platforms approved for storing sensitive documents in the cloud.
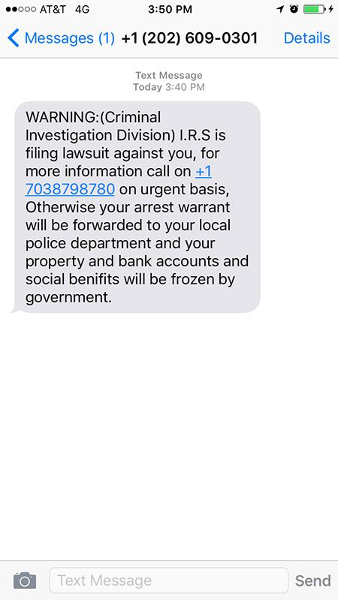
Warning From the U.S. Department of Education
Federal Student Aid (an office of the U.S. Department of Education), has issued a warning related to an ongoing IRS impersonation scam, as seen here and copied below. Students and employees at institutions with ".edu" email addresses are particularly at risk of being targeted with these scams. SPU students, faculty, and staff should be watchful of for any emails that appear to be from the IRS and claim to disclose information about your "tax refund payment" or "recalculation of your tax refund payment." If you receive an email like this, please delete it and do not click on any links. Contact CIS with any questions.
Notice from the U.S. Department of Education follows:
The Internal Revenue Service (IRS) posted a warning of an ongoing IRS impersonation scam that appears to primarily target educational institutions, including students and staff of institutions that have ".edu" email addresses.
The Treasury Inspector General for Tax Administration and IRS Criminal Investigation has been notified about the suspicious emails that display the IRS logo and use various subject lines, such as "Tax Refund Payment" or "Recalculation of your tax refund payment." The emails ask individuals to click a link and submit a form to claim their refunds.
The phishing website requests that taxpayers provide the following information:
Social Security Number (SSN)
First Name
Last Name
Date of Birth
Prior Year Annual Gross Income
Driver's License Number
City
State/U.S. Territory
ZIP Code/Postal Code
Electronic Filing PIN
The U.S. Department of Education encourages institutions to visit the IRS web page—irs.gov/newsroom/irs-warns-university-students-and-staff-of-impersonation-email-scam—which contains details about the phishing campaign. We also ask that you share the web page widely with students and staff to raise awareness about this scam.
Recipients of this scam email should not click on the link in the email, but they can report it to the IRS. For security purposes, recipients should save the email using the "save as" feature and send that file as an attachment or forward the email as an attachment to phishing@irs.gov.
Taxpayers who believe they may have provided identity thieves with their information should consider immediately obtaining an Identity Protection (IP) PIN. An IP PIN is a six-digit number that helps prevent identity thieves from filing fraudulent tax returns in a victim's name. This is a voluntary IRS opt-in program.
Taxpayers who attempt to e-file their tax return and find it rejected because a return with their SSN already has been filed should file an IRS Form 14039, Identity Theft Affidavit, to report themselves as a possible identity theft victim. To learn about the signs of identity theft and actions to take, visit the Identity Theft Central web page on irs.gov.
If you believe your institution has been targeted or breached, report the incident immediately to CPSSAIG@ed.gov and FSASchoolCyberSafety@ed.gov. Include the following:
Name of the institution
OPEID – School Code
Date the incident occurred (if known)
Date the incident was discovered
Technical details of the incident (if known)
Extent of the impact
Remediation status (what has been done since discovery)
Institutional points of contact
Thank you for your attention to this matter. Federal Student Aid is committed to working with institutions to combat cybersecurity attacks and protect student financial aid information. If you have questions about the information included in this announcement, please email FSASchoolCyberSafety@ed.gov or call 202–377–4697 between 7 a.m. and 5 p.m. Eastern time Monday through Friday. We look forward to working with you and thank you in advance for your efforts to safeguard student information and secure your institution.
October 2020 is the 7th year of National Cybersecurity Awareness Month (NCSAM). NCSAM continues to raise awareness about the importance of cybersecurity across our Nation, ensuring that all Americans have the resources they need to be safer and more secure online.
The Department of Homeland Security and the National Cyber Security Alliance (NCSA) are proud to announce this year’s theme: “Do Your Part. #BeCyberSmart.” This theme encourages individuals and organizations to own their role in protecting their part of cyberspace, stressing personal accountability, and the importance of taking proactive steps to enhance cybersecurity. NCSAM emphasizes “If You Connect It, Protect It.”
For each week of Cyber-Security Awareness Month, CIS will present a short but entertaining video emphasizing simple steps you can take to #BeCyberSmart! Take these steps so, "If you connect it, you can Protect it," both at work and at home. These videos were produced by Adobe in conjunction with the National Cyber Security Alliance (NCSA) staysafeonline.org where you can find a wide range of topics, to include information and resources to share with your kids to help keep them safe in this digital world.
Do Your Part. #BeCyberSmart
Security Awareness Week 1: Passwords
Passwords provide the first line of defense against unauthorized access to your computer and personal information. The stronger your password, the more protected your computer will be from hackers and malicious software.
Double your login protection. Enable multi-factor authentication (MFA) to ensure that the only person who has access to your account is you. Use it for email, banking, social media, and any other service that requires logging in. If MFA is an option, enable it by using a trusted mobile device, such as your smartphone with an authenticator app like DUO!
Shake up your password protocol. According to NIST guidance, you should consider using the longest password or passphrase permissible. Get creative and customize your standard password for different sites, which can prevent cybercriminals from gaining access to these accounts and protect you in the event of a breach. Use password managers to generate and remember different, complex passwords for each of your accounts.
Security Awareness Week 2: Data Handling
The use of data helps make our lives more convenient and streamlined which likely means the proliferation of online data and devices are here to stay. There is one best practice that each of us can apply that will help personal data stay more secure – only share on a need-to-know basis.
Never click and tell. Limit what information you post on social media—from personal addresses to where you like to grab a coffee. What many people don’t realize is that these seemingly random details are all that criminals need to know to target you, your loved ones, and your physical belongings—online and in the real world. Keep Social Security numbers, account numbers, and passwords private, as well as specific information about yourself, such as your full name, address, birthday, and even vacation plans. Disable location services that allow anyone to see where you are—and where you aren’t—at any given time.
Stay protected while connected. Before you connect to any public wireless hotspot—such as at an airport, hotel, or café—be sure to confirm the name of the network and exact login procedures with appropriate staff to ensure that the network is legitimate. If you do use an unsecured public access point, practice good Internet hygiene by avoiding sensitive activities (e.g., banking) that require passwords or credit cards. Your personal hotspot is often a safer alternative to free Wi-Fi. Only use sites that begin with “https://” when online shopping or banking.
Security Awareness Week: 3 Computer Theft
Having something stolen from you tends to leave an indelible feeling of violation and injustice. If what is stolen is an electronic device (e.g. laptop, phone, flash drive), not only is the property gone but so is your data. Stolen data can be a more damaging long term than the loss of the physical device itself. The data could be personal or company data. If the device is able to be used by the thief, there are many ways the device can become of value.
The most important best practice is to not leave devices unattended in public places. This includes a locked car. In many cities, car break-ins are extremely common. Even if you think your risk might be lower, don’t take a chance. Take your devices with you!
Security Awareness Week: 4 Phishing and Ransomware
Phishing, we’ve heard of it, but what does it mean? In summary, it is a tool and method attackers use to try and coerce people into clicking on a malicious site or download, potentially leading to a security issue.
Ransomware is an especially dangerous consequence of falling for a phishing attempt. Ransomware is software that locks down data by encrypting it and won’t be unlocked through decryption until a ransom is paid. To protect yourself from ransomware:
- Be wary of suspicious emails and look for the signs.
- Make sure your antivirus software is up to date and running. It’ll help stop the ransomware in its tracks.
- If ransomware is installed, then if you’ve backed up your data, you can ignore the threat and restore the data. Unfortunately, in many cases and especially for large enterprises, the cost of the ransom is significantly less than the cost to restore the data, even if it’s backed up. Therefore, the first and second layers of protection are critical.
Bonus Episodes:
Removable media
Removable media and devices are portable hardware. The most common is a USB flash drive but other forms could be an external hard drive or SD card.
When it comes to cybersecurity best practices, removable media and devices must only be plugged or inserted into your computer if you trust/know the source.
Vishing Scams
Security Awareness is not just for computers. “Vishing” which is defined as the fraudulent practice of making phone calls or leaving voice messages purporting to be from reputable companies in order to trick individuals to reveal personal information, such as bank details and credit card numbers.
How to spot a vishing scam
Here are some of the tell-tale signs of a vishing scam:
- The caller claims to represent the IRS, Medicare, or the Social Security Administration. Unless you've requested contact, none of these federal agencies will ever initiate contact with you by email, text messages, or social media channels to request personal or financial information. In fact, be skeptical of anyone who calls you with an offer.
- There's a frantic sense of urgency. Scammers will try to tap into your sense of fear, using threats of arrest warrants and problems with your account. If you get one of these phone calls, remain calm and never give out your own information. Hang up and do your own investigation.
- The caller asks for your information. They may ask you to confirm your name, address, birth date, Social Security number, bank account info, and other identifying details. To trick you into thinking they're legit, they may even have some of this info on hand. The goal is to get the remaining info that they don't have yet.
CIS HelpDesk Support and Hours
If you have questions or need more information
Submit a Helpdesk Request via the Portal: www.spu.edu/cishelpdesk
The CIS HelpDesk can be reached by phone at (206) 281-2982
Monday – Friday 7:30am – 5:00pm
Email any time at help@spu.edu
Office Hours
Monday - Friday 7:30 a.m. - 5:00 p.m.
Due to COVID-19 Protocols, In-Person support is available by appointment only.
(Contact the HelpDesk or submit a HelpDesk Request to make an appointment)